Brilliant CTF by Counter Hack team as usual. Tons of good fun, awesome challenges and a great story to go with it. Whats not to like?
Here’s a quick write-up on the answers I produced on the 2016 challenge.
1) What is the secret message in Santa’s tweets?
I wrote a simple Javscript to extract all the Tweets. All this script does is to concatinate all the tweet bodies into a single variable, then outputting the variable into the browsers console.
msg = ""
for (i = 0; i < document.getElementsByClassName('tweet-text').length - 1;i++) {
msg += document.getElementsByClassName('tweet-text')[i].innerHTML + '\n'
}
console.log(msg)
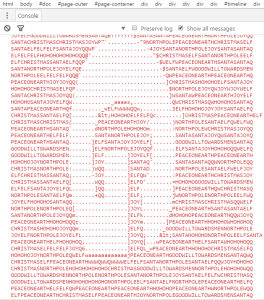
This produces the following output:
We can see that the output represents ASCII art character G. In total, the answer produced the string “BUG BOUNTY”.
2) What is inside the ZIP file distributed by Santa’s team?
The Instagram account of Santa had an image linking to a zip file. Simply download the ZIP file from the target webserver and inspect the file. The password was simply the string from the #1.
3) What username and password are embedded in the APK file?
Simply look through the resources files and configuration and you will see the credentials guest / busyreindeer78.
4) What is the name of the audible component (audio file) in the SantaGram APK file?
The audio file was in the resources\raw folder. It’s name was discombobulatedaudio1.
5) What is the password for the “cranpi” account on the Cranberry Pi system?
Procedure:
- Download the Cranberry PI image
- Use fdisk to review the partitions
- Mount the partitions
- Crack the passwords in the /etc/shadow file using JTR or Hashcat with the Rockyou dictionary file.
- This cracked into two different passwords:
- pi:thenorthpole07
- cranpi:yummycookies
6) How did you open each terminal door and where had the villain imprisoned Santa?
Door 1
We are presented with a shell and something to look for. Using the “find .” command.
This reveals several hidden files, one which is of our interest: elf@3030ec3eb5a9:~/.doormat/. / /\/\\/Don’t Look Here!/You are persistent, aren’t you?/’
From here we just had to cat the correct file, keeping in mind escaping the special characters such as “.!’\ “.
Door 2
Basically I just read the manual and defeated the wumpus by remembering the cave layout and the different options.
Door 3
The shell we’re in is less or more, and it supports command execution. By entering the command !/bin/bash , this gives us a proper shell, which we can now use to see all the files involved. One of the files was the source code to run the train, which also contained the password.
Door 4
We are in a shell with a pcap in the current directory. We don’t have read access to pcap, but sudo -l reveals that we can access it through the itchy user like this: sudo -u itchy strings out.pcap. This yields half of a flag, but not the rest. The rest of the flag is hidden in a transmission of an ELF file. Using strings -e l out.pcap revealed the second half of the flag.
Door 5
A dialog from the movie Wargames, between the main actor and the Wooper computer, was displayed, missing out the information from the actor. Simply typing what the actor would type in to the Wooper computer yielded the flag.
Door 6
With the 7 audio files in place, they were put into order, based on their track numbers. The speed of the audio was then sped up to about 700-800%, and the audio could then be understood. Removing the background noise also helped.
7) For each of the six items, which vulnerabilities did you discover and exploit?
The Mobile Analytics Server (via credentialed login access)
Simply log on to the solution using the guest / busyreindeer78 credentials, then click the Mp3 menu item.
The Dungeon Game
I googled walkthroughs for this game, and figured out a cheat command called the GDT, presumably named after the “Global Descriptor Table”. From here I could access all rooms, resources and what not. I identified the dialog and rooms necessary to get the password through the GDT.
The Debug Server
Activated the debug flag in the APK file, re-build and installed it onto my device. I then observed through Proxy the traffic going to the debug server. This traffic was then modified using the Burp Repeater. The JSON response revealed an interesting parameter called verbose, and this was set to false. Setting the verbose flag to true in the request makes the response suddenly give away a lot more information, among other things, a files array containing the mp3 we want.
The Banner Ad Server
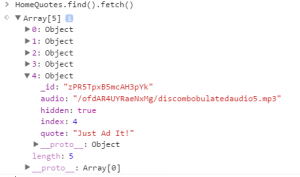
The MeteorMiner Greasemonkey/Tampermoneky script by Tim Medin was used to browse what the Meteor application is exposing. The Home Quotes object had 5 records in them, while only 4 was shown as quotes on the front page. 1 quote was different and had an audio attribute on it. The HomeQuotes object was printed with the browsers console, and one could easily see the mp3 file hidden inside the object:
The Uncaught Exception Handler Server
The calls to the exceeption server was intercepted with burpsuite, revealing a JSON post request to exception.php. The request contained WriteCrashDump, and this was changed to ReadCrashDump to see what happened. From here, a simple tutorial of error messages gave us clues for the request we needed to create to make the script parse it properly. The request ended up like this, but it did not work for parsing other php files, such as index or exception:
{“operation”:”ReadCrashDump”, “data”:{“crashdump”:”crashdump-YhFSnH”}}
Instead, adding the stream handler convert.base64-encode, we could now read the contents of the files we wanted.
{“operation”:”ReadCrashDump”, “data”:{“crashdump”:”php://filter/convert.base64-encode/resource=exception”}}
This gave us an base64 result of the source code of exception.php, where the mp3 filepath was hidden in a php comment.
The Mobile Analytics Server (post authentication)
Running nmap with default scripts reveals a git repository hosted at this site. Downloading and repairing the repository lets us browse the source code of the page and also the database SQL build script.
Logging onto the analytics server as administrator with a password previously leaked, we could access more functionality. Specifically we could query for information, view and edit previously made queries. By first creating a simple query and specifying to save it, we could give the edit script the appropriate GUID to edit it. The log then tells us a hint, that it is checking for id, name, description, and finally, a query. The form only allows us to input id, name and description, but the script also parses the query parameter. Setting the query parameter to select * from audio allows us to see two audio files in this database, one which we already have. Using the query select to_base64(mp3) from audio where username = ‘administrator’ allowed us to copy the base64 encoded value of the mp3 data into a txt file. This was simply decoded using the command line: base64 –decode < mp3.txt > mp3.mp3
8) What are the names of the audio files you discovered from each system above? There are a total of SEVEN audio files (one from the original APK in Question 4, plus one for each of the six items in the bullet list above.)
- discombobulatedaudio1.mp3
- discombobulatedaudio2.mp3
- discombobulatedaudio3.mp3
- debug-20161224235959-0.mp3
- discombobulatedaudio5.mp3
- discombobulated-audio-6-XyzE3N9YqKNH.mp3
- discombobulated-audio-7.mp3
9) Who is the villain behind the nefarious plot.
Apparently Doctor Who. LoL!
10) Why had the villain abducted Santa?
To prevent the movie “Star Wars Holiday Christmas” being released.