Cyber Security Blog of Chris Dale
-
Why it’s easy being a hacker – A SQL injection case study
Finding SQL injections today is like picking apples from an apple tree. It’s very easy, and anyone can do it. Ask any hacker you want, SQL injection is everywhere. There have been many folks predicting the end of SQL Injection, however, year after year we see it in the OWASP Top 10.
-

SANS Hacker Techniques, Exploits & Incident Handling kommer til Bergen! (Norwegian)
I 2013 tilbyr SANS mentor basert studium her i Bergen, oppstart 6. Mars. Kurset som avholdes er det meget kjente “SEC504: Hacker Techniques, Exploits & Incident Handling” utviklet av den velkjente sikkerhetsguruen Ed Skoudis. Kurset gir studenten god ryggdekning til å bli sertifisert ved å bestå GCIH eksamen(GCIH – GIAC Certified Incident Handler). Mentor er…
-

Evolution of the Nmap source code
This awesome codeswarm of the Nmap sourcecode shows the development of Nmap from 2005 to todays date. Pretty impressive development history, and also fun to watch!
-
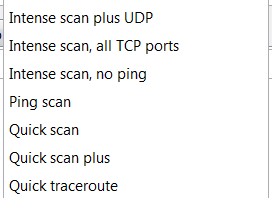
Nmap preset scans – Options and scan types explained
Zenmap is the GUI for the very popular free port scanner Nmap. It comes pre loaded with 10 different scan types which we will take closer look at them in this article. Some of the scan types are kind of obvious, however they may not be to everyone.
-
Handy SQL queries
Finding filetypes stored in a MySQL table If your system allows fileuploads, and you have a database table where you store all the fileuploads, it could be interesting to see what types and how many types of files are being uploaded to your system. This query will find all filetypes uploaded to the system. Replace…
-
Distribuert tjenestenekt: «Fordi vi kan» (Norwegian)
Hvordan kan det ha seg at en liten gruppe tenåringer klarer å ta ned store nettsider både i Norge og utlandet? Jeg tar en nærmere titt på hvordan slike angrep kan utføres fra gutterommet til en fjortenåring.
-
Frustrations with Microsoft LiveID sign-on
Today I decided to sign up for Microsoft security bulletin notifications as I am working alot in windows enviroments now and it is important for us to get security patches out there as soon as possible. The list of security notifications can be accessed through 3 options (which can be found here: http://technet.microsoft.com/en-us/security/dd252948) : Email RSS…
Looking to get in touch?
