Category: Tips & Tricks
-
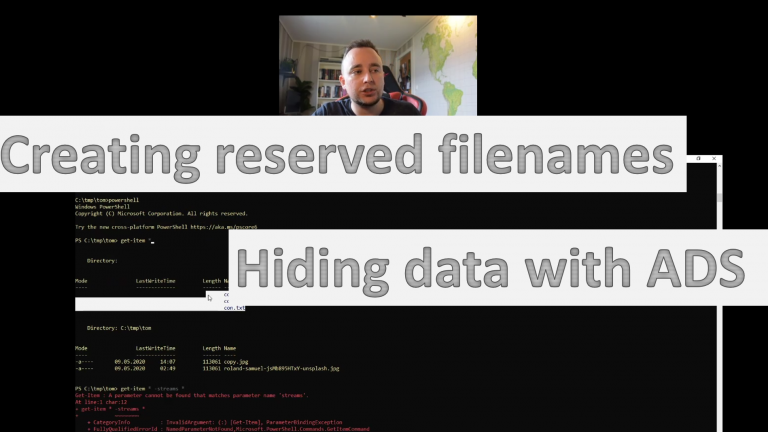
Creating reserved file names and Alternate Data Streams
I created a Youtube video to prove how to create reserved file names using the \\.\ prefix in the command line. Also I show how to append ADS to facilitate hiding and other interesting stuff.
-

Netcat backdoor without -e and mimicking Netcat with bash
Netcat backdoor without -e (execute option) Netcat is installed by default on a lot of Linux systems, however we are seeing more and more Netcat’s are compiled without the -e option. The -e options allows us to execute and serve an executable over the connecting socket. It is incredibly handy feature, both for controlling an executable over a network connection,…
-

Audio reminder for when computer is back online
This handy little command reminds me by audio when my computer is back online. I just had a 30 minute Internett outage, and it was nice to get right back to my seat when my computer started bleeping out alarms. for /l %i in (1,0,2) do @ping -n 2 8.8.8.8 2>1>nul && @powershell -command [System.console]::Beep(300,1000)…
-

Detecting if Volume Shadow Copies has been explicitly disabled through registry
Ransomware is very fond of disabling Volume Shadow Copies when infecting targets. Here is a script to remotely detect if Volume Shadow Copies has been disabled. First, we use PSExec from Microsoft Sysinternals and a local reg query command. This is useful if you only have a list of IP addresses, not hostnames of the…
-

Mapping attack surface for Ransomware / Cryptolocker
With all the ransomware hitting everyone, everywhere, I decided to share my scripts on how I map the attack surface of internal threats, and subsequently ransomware / cryptolocker. It is not fully automated yet, but hopefully sharing this will give people the right ideas, and perhaps some might even automate it. For now, this only…
-
Using Powershell to fetch file hashes with multiple algorithms
You might need to check file hashes across multiple directories and across multiple algorithms, e.g. verifying all files hashsums against both MD5 and SHA1. This is an example of how to accomplish such task using Powershell. The command you run is: gci -Recurse | select FullName |…
-

Remotely lock a computer, and prevent them from logging back in
Sometimes you have to throw someone off a terminal, but at the same time preserve the evidence on the terminal. For example if someone is using a terminal to hack something, and you need to secure the running terminals to capture the commands that has been run. It is quite simple to accomplish this, as…
-
Finding files and grepping for information
Sometimes you have to find interesting files, then grep through those specific files dynamically. With Linux this is as easy as: find . -name
-exec grep -i -H {} \; This will simply recursively look for files you want to find, e.g. *.txt, and for each file found, grep that file for whatever… -
Slow DNS enumeration
Fierce is an excellent tool for doing DNS reconnaissance, i.e. querying the DNS server for potential domain names to be revealed. I’ve seen some setups where the enumeration has gone horrible slow. If your DNS enumeration tool is going slow, fire up tcpdump and inspect the DNS traffic. tcpdump -i
-nn port 53 Normally…