Category: Blog
-
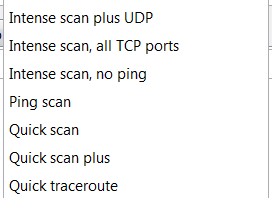
Nmap preset scans – Options and scan types explained
Zenmap is the GUI for the very popular free port scanner Nmap. It comes pre loaded with 10 different scan types which we will take closer look at them in this article. Some of the scan types are kind of obvious, however they may not be to everyone.
-
Handy SQL queries
Finding filetypes stored in a MySQL table If your system allows fileuploads, and you have a database table where you store all the fileuploads, it could be interesting to see what types and how many types of files are being uploaded to your system. This query will find all filetypes uploaded to the system. Replace…
-
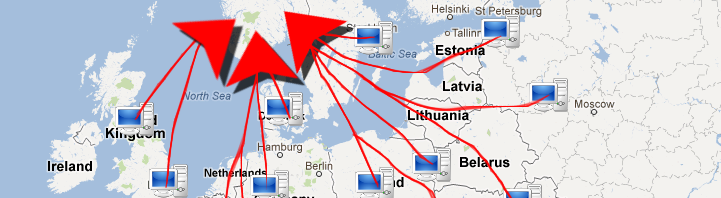
Distribuert tjenestenekt: «Fordi vi kan» (Norwegian)
Hvordan kan det ha seg at en liten gruppe tenåringer klarer å ta ned store nettsider både i Norge og utlandet? Jeg tar en nærmere titt på hvordan slike angrep kan utføres fra gutterommet til en fjortenåring.
-
Frustrations with Microsoft LiveID sign-on
Today I decided to sign up for Microsoft security bulletin notifications as I am working alot in windows enviroments now and it is important for us to get security patches out there as soon as possible. The list of security notifications can be accessed through 3 options (which can be found here: http://technet.microsoft.com/en-us/security/dd252948) : Email RSS…
-
Can you use ONE WORD to describe the most important information security solution in your arsenal
One word On LinkedIn there was a word game in the group “Information Security Community“. The deal was to name what you think is the single most important thing in IT security. The now over 1 year old discussion is still active and keeps popping up in my LinkedIn newsletters. While I do not agree…
-
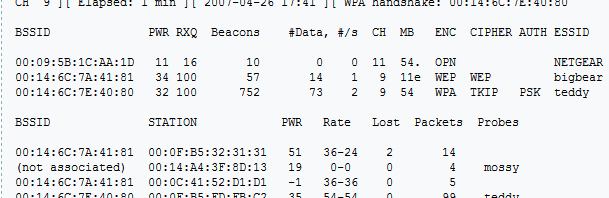
Enumeration with practical examples from SQLMap
SQLMap – http://sqlmap.sourceforge.net/ SQLMap is an open source and free automatic SQL injection and database takeover tool. I’ve found it extremely usefull for doing blind SQL injection as it is normally extremely tedious work to get it done quickly. However for this article I will only cover the enumeration function.
-
Unlocking locked laptop – From physical access to recovering NT hashes
A friend of mine worked at the IT department of a school and we had a talk about what consequences it may have if a laptop without disk encryption got into the wrong hands. He could not see what the big deal was if a student computer got lost so I suggested that if he…
